

I would almost say that Broadcom is probably worse off than most of the rest in your list combined. 😠


I would almost say that Broadcom is probably worse off than most of the rest in your list combined. 😠


I have Wemo light switches, outdoor plugs, mini plugs, and the original plug. Since they are HomeKit enabled you don’t have to set them up with the Wemo app. You can set them up directly from HomeKit. I’ve never downloaded a Wemo iOS app.
Sucks that they aren’t supported anymore but my warranty ran out a while ago. I may lose firmware updates with patching for security vulnerabilities but I have these running on an IOT VLAN that is very restricted and only has the access that my firewall lets it access.
You aren’t a moron at all. If you haven’t been exposed to it I wouldn’t expect you to know what it is.
So virtualization is kind of like taking multiple computer operating systems and running them on one physical server. So instead of needing a physical server for each system, you can run dozens. Then you can have clusters of physical machines that are running hundreds of virtual machines (computers) per cluster.
As a virtualization engineer, I work with VMware products (Now owned by Broadcom) to design and implement virtual infrastructure. This allows organizations to run multiple virtual machines on fewer physical servers, which enhances scalability and simplifies backup and recovery processes. Think of it as creating a digital version of a computer that can be easily adjusted and moved around.
Virtualization Engineer. Finally doing what I am passionate about. I was a stock broker 10 years ago. It was a crazy ride.


So I’m not sure if this is the problem affecting your friend, however, RCS messaging uses additional ports rather than just the standard tcp/443 port to send traffic. This port is specifically tcp/5223. If your friend connects to a wireless network that has a firewall that doesn’t have the port open, then the RCS messages will fail to send/receive until they are either connected to their cellular network or a wireless network that doesn’t have that port blocked.
The catch is, if you try to send a message while you are on a network where the traffic isn’t allowed, the RCS message doesn’t attempt to resend right away after changing to a network where the traffic is allowed.
I have a firewall in my house that has very strict rules and I had to enable a firewall policy to allow this traffic to be able to send / receive RCS messages when I was connected to my home’s WiFi. My wife’s company WIFi network has that port blocked so she doesn’t connect to it anymore and RCS works just fine.
If you want to see if this is the case for your friend’s phone, have them use their mobile network while sending / receiving RCS messages to test.


No it has not. Validated on Ubuntu 16.04, 18.04, 20.04, 22.04 running CrowdStrike Sensor


Windows Server OSes running CrowdStrike affected too


This VPN protocol usually uses a private key (client) / public key (server) combo that is used to connect through a public IP address (the 2 nodes can’t communicate it without) using the specified TCP or UDP (more often lately) and port to create the VPN tunnel that’s gets established during the handshakes.
There is a whole lot more going on with the process but that’s a high level view. But I have a WireGuard VPN service running on a raspberry pi that I put in a DMZ on my perimeter firewall.
But a port scanner would be able to see that port is open. Make sure you keep your software up to date. Hopefully the software devs of the VPN application is keeping their stuff up to date to avoid any vulnerabilities getting exposed in the code and a backdoor getting created because of it. As long as that doesn’t become an issue, no one will be able to get through without the private key. And those are usually uncrackable in a lifetime with the complexity and length of the key.


Glad I could help! 😃


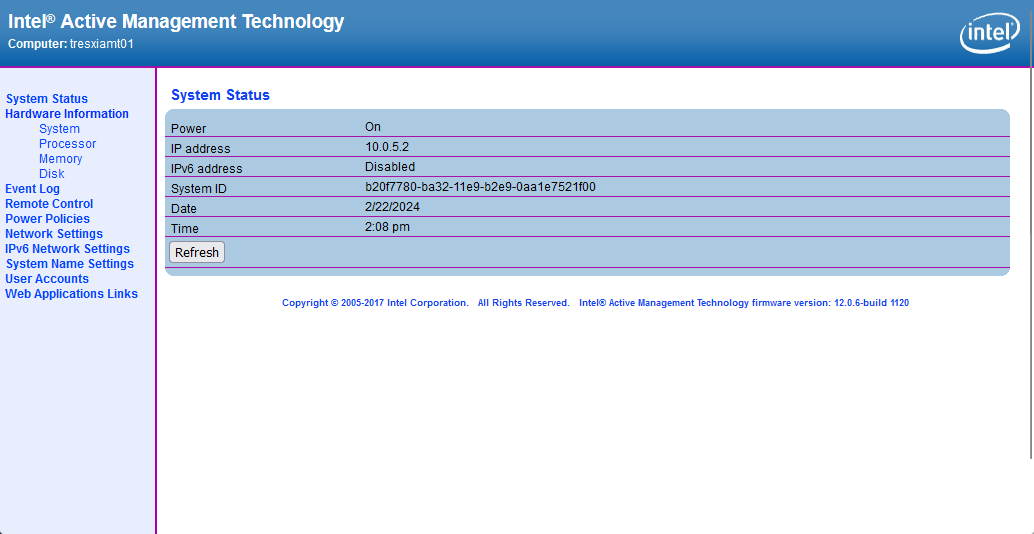
Ok, I grabbed a few screen shots for you as well. Here is a site that will link you to MEBx setup that enables AMT: http://h10032.www1.hp.com/ctg/Manual/c03883429
When power on your ProDesk G3, you can access the MEBx setup by pressing Ctrl+P or they also say F6 or Escape will get you there. Intel AMT runs on a different IP address than what your OS gets. You can assign DHCP or a static IP address and setup your admin password. You can then access the portal from http://ipaddress:16992 There should be a method of access what would show on the screen through a KVM like access but I use MeshCentral for that so I couldn’t tell you how to do it without.
Hopefully, that gives you a start. Feel free to reach back out if you have any questions. Thank you!



I’m not in front of my computer atm, but I think I have something that can help you out. I have a 3-node Lenovo Thin client cluster that I manage their KVMs using the Intel vPro. I even went a step further using MeshCentral running on a VM to centralize my KVM access since I have 3 of them, but that’s another story.
Anyway, I’ll see if I can grab you some URLs in the morning if someone else doesn’t beat me to it or you find it on your own running google queries.


2024 - Mexicans at the border (you know it’s already happening)


3-Node ESXi cluster with 10 Debian VMs, 3 Windows VMs, and one FreeBSD VM


deleted by creator


deleted by creator


They call it a tcpdump but Wireshark analyzes all network traffic. You can use the udp.port == 51820
Do you have a laptop? Probably more tools and easier to test from there.


Meant to say if you still get stuck, run Wireshark on your FW and your VPS and run a tcp dump and filter the traffic to see where the data stops.
You can also use traceroute to your public IP on the port 51820 and check your connectivity or even curl: -v http:////publicip:51820


Did you setup a NAT on the firewall? You have to setup a static NAT on the interface that your Public IP sits on and to the private IP address of your VPS (you are using a private network space from one of the other interfaces on your FW right?).
Make sure that the policy that you create with the NAT includes UDP 51820 (unless you changed the default port) People often mistake using TCP which is a different protocol. If that doesn’t work, then look at the traffic on your FW
There are good people and bad people all around the world. The bad people sometimes tend to be a little bit louder than the good people and sometimes drown out the people that are kind and genuinely do care about others.
So while, no, I’m not going to tell you that there are not a lot of bad people in the world we live in. There are good people too. Pick and choose the people that you surround yourself with and surrounding your self with kind people can make a world of difference.